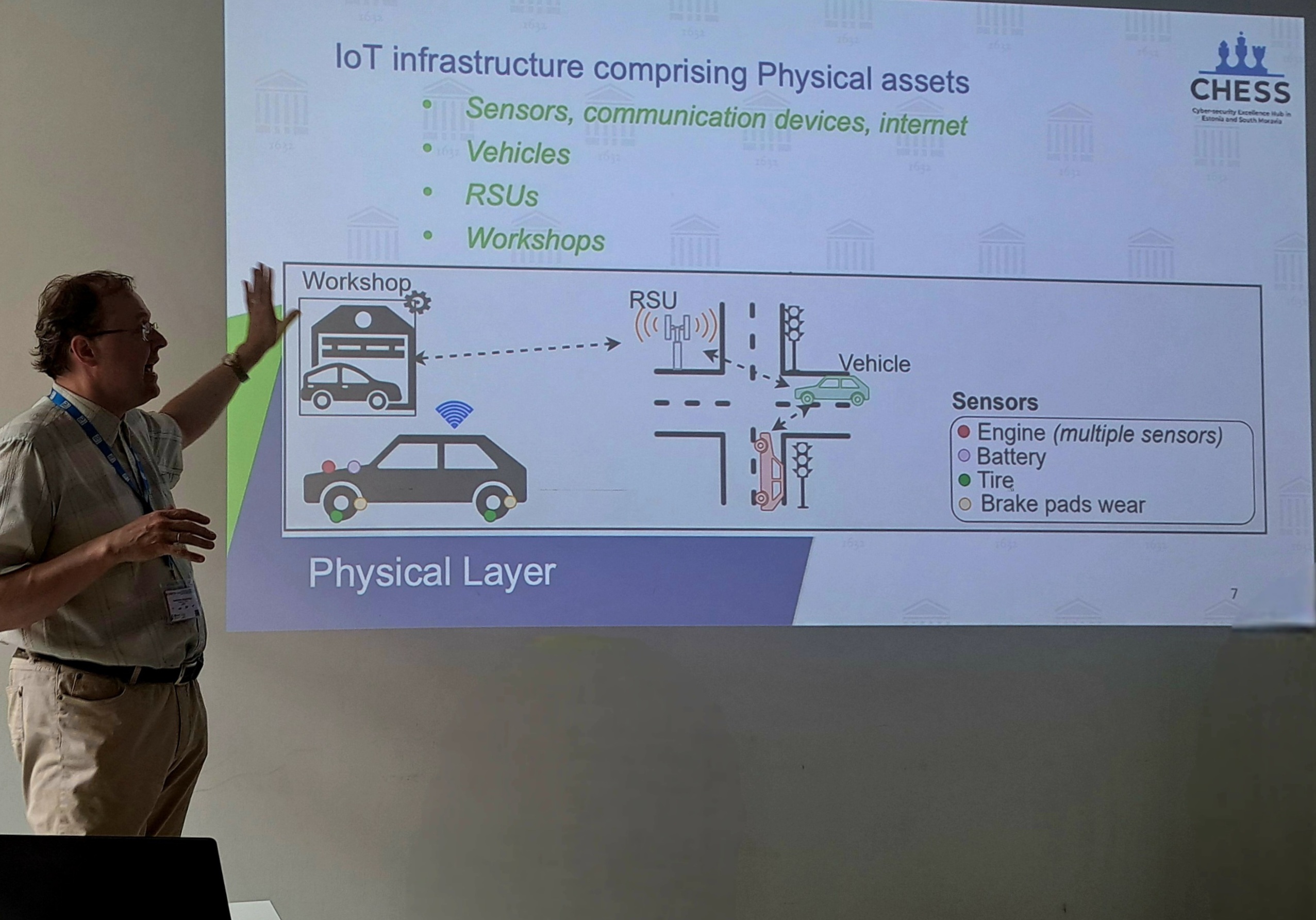
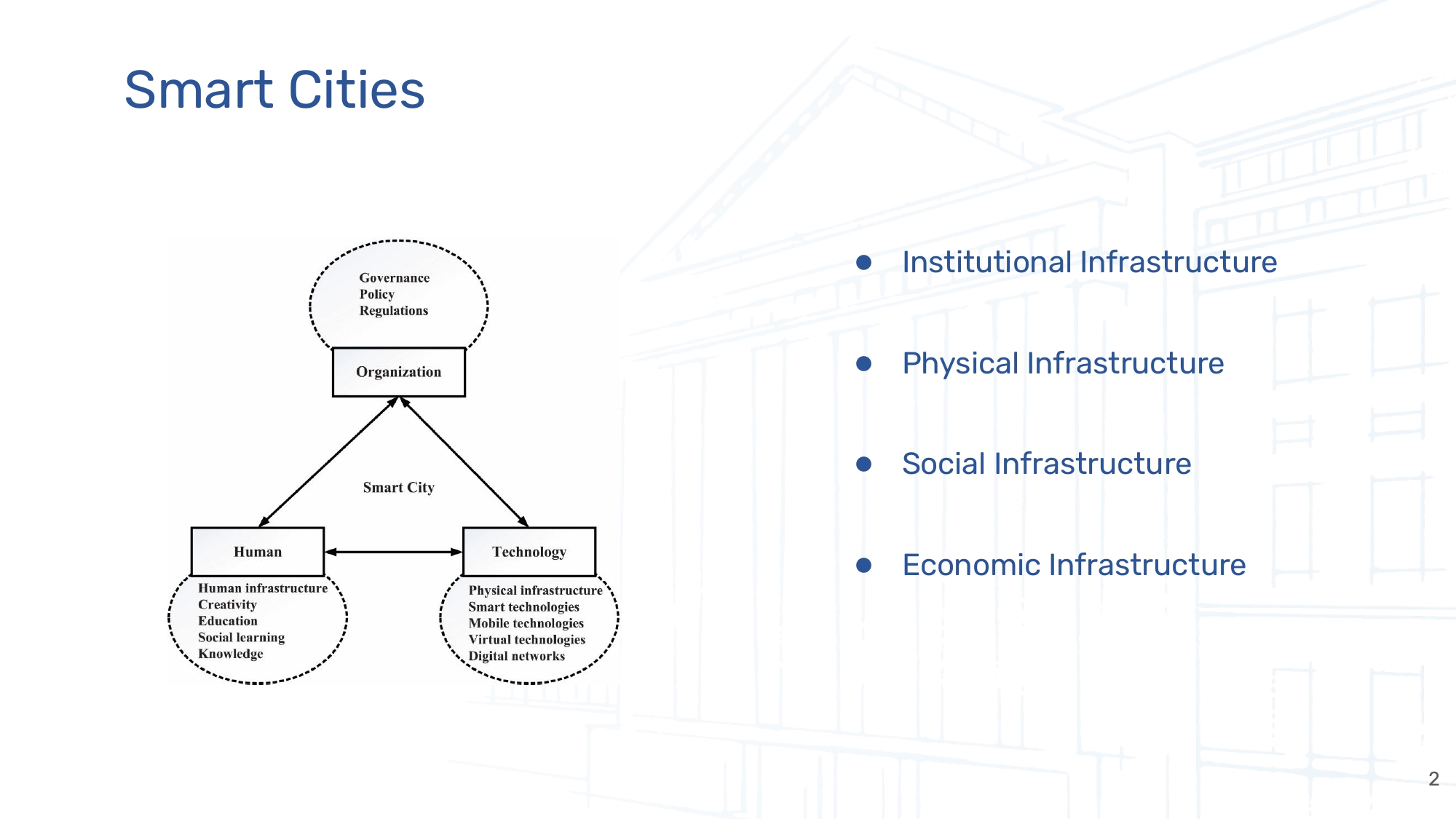
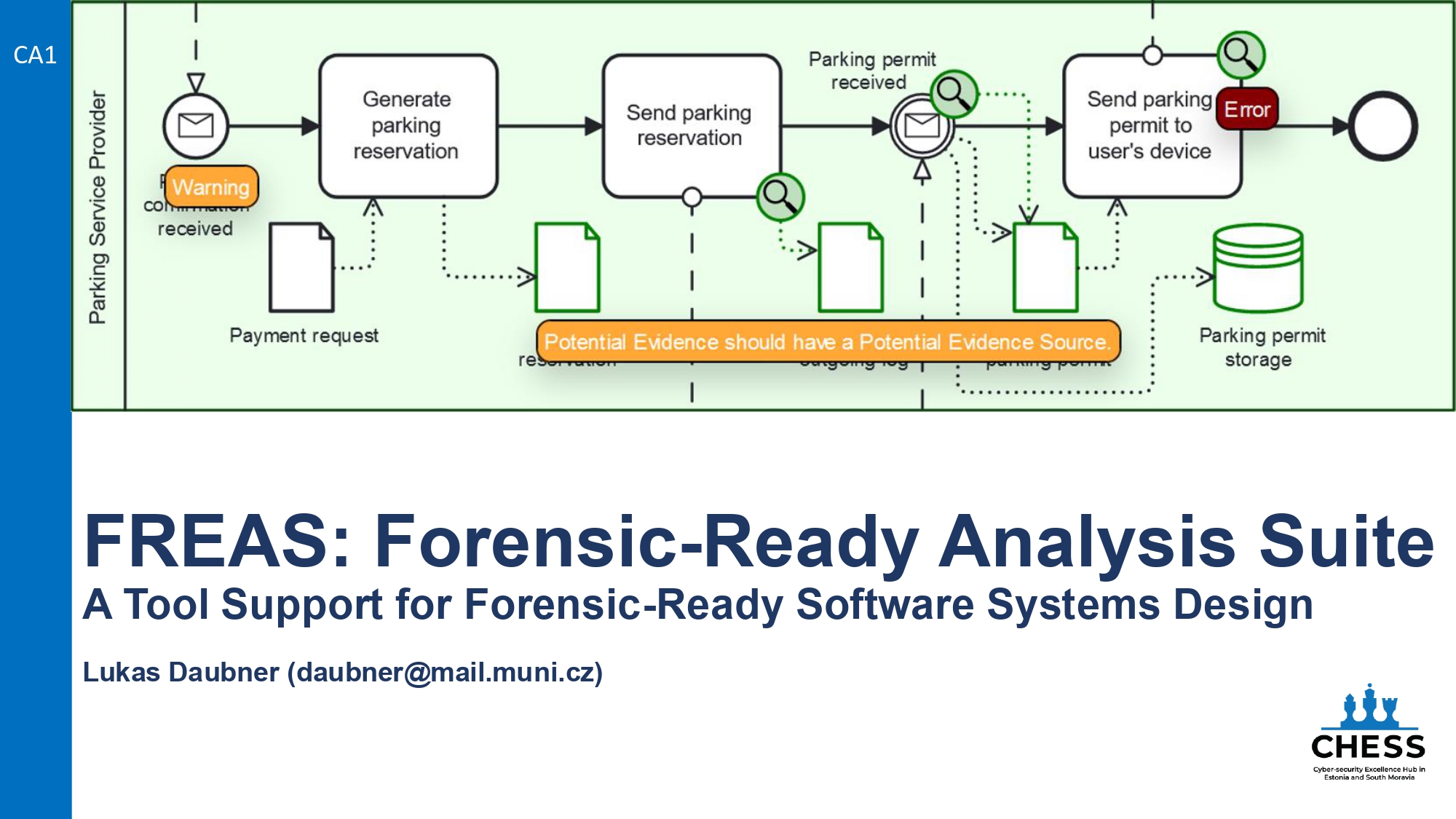
Inspiring Cyber-security Dialogues: Access our impactful presentations, bridging the gap between research and real-world solutions.
2026
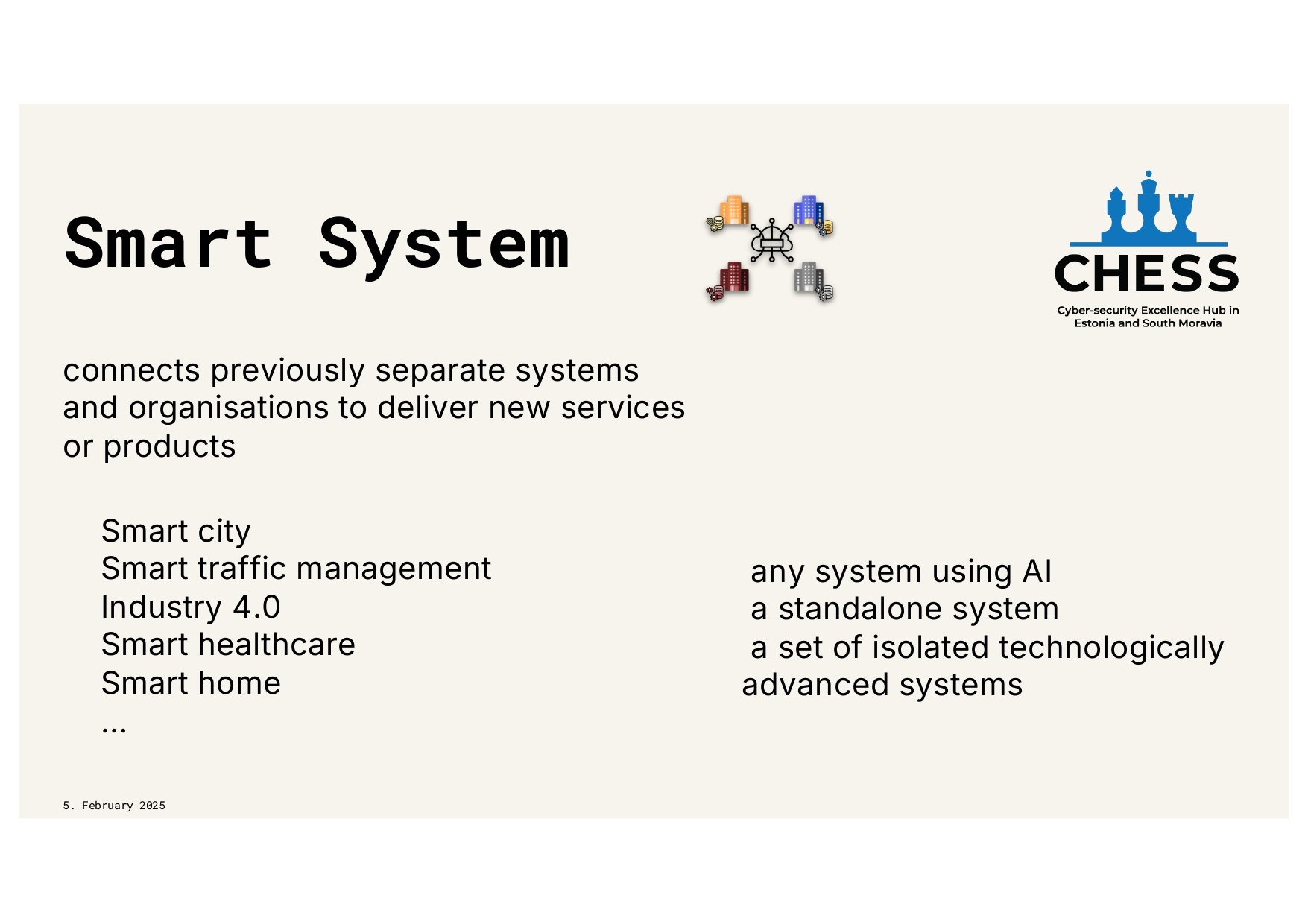
2026: Another Year of Enlightening Cyber-security Dialogues has started. Access presentations that encapsulate the year’s most influential talks, workshops, and conferences, driving the conversation forward.
2025
2025: Another Year of Enlightening Cyber-security Dialogues has started. Access presentations that encapsulate the year’s most influential talks, workshops, and conferences, driving the conversation forward.
2024
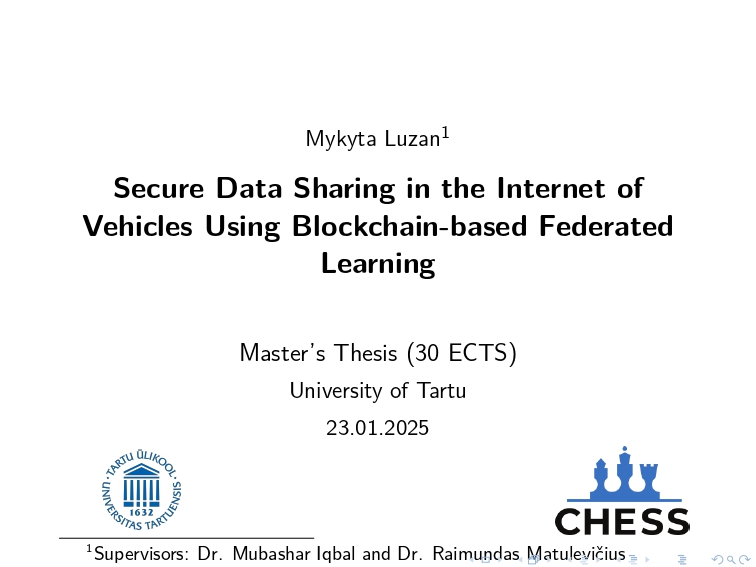
2024: Another Year of Enlightening Cyber-security Dialogues. Access presentations that encapsulate the year’s most influential talks, workshops, and conferences, driving the conversation forward.
2023
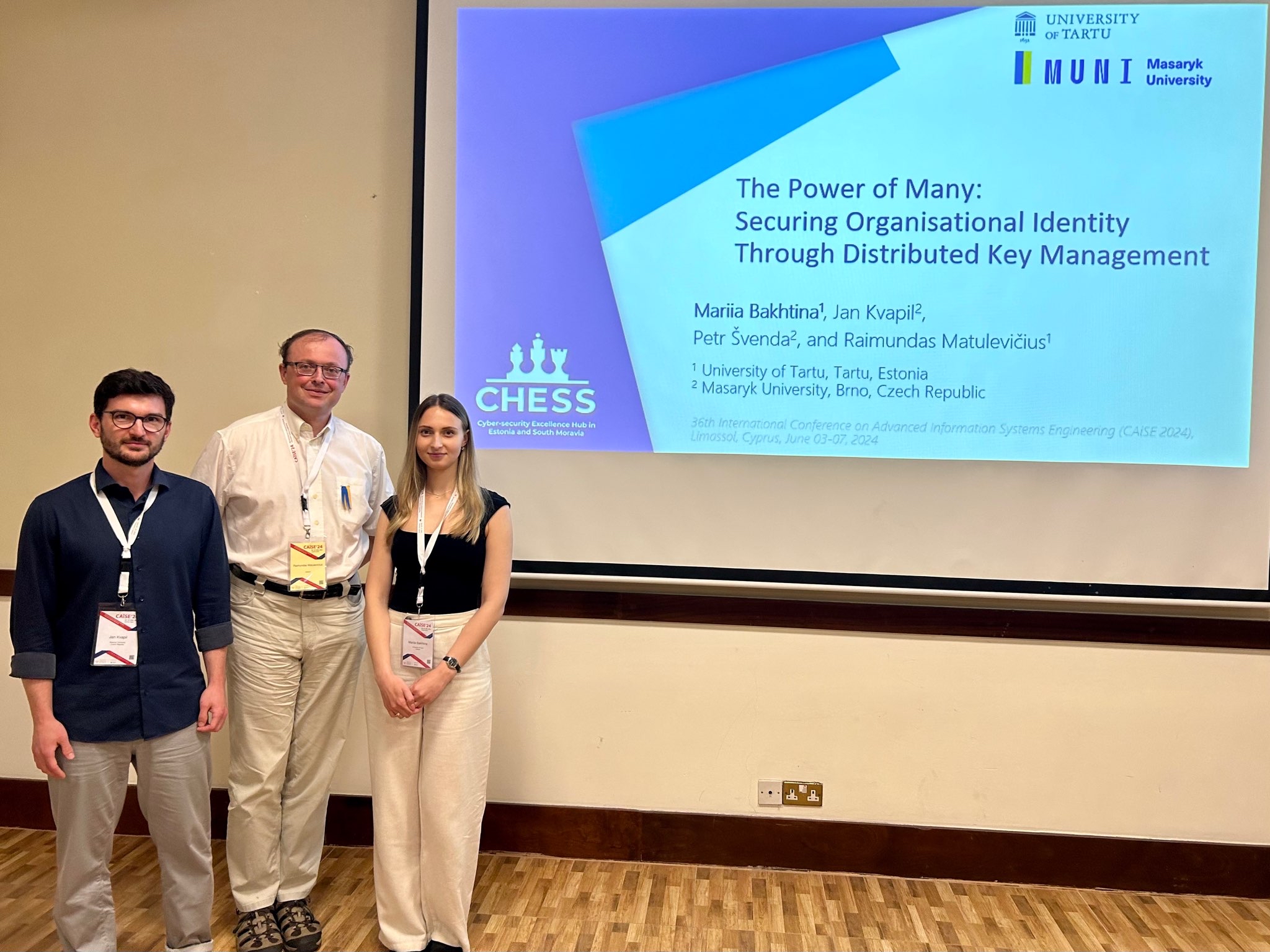
2023: A Year of Enlightening Cyber-security Dialogues. Access presentations that encapsulate the year’s most influential talks, workshops, and conferences, driving the conversation forward.